Technology | 5 Minutes Reading
Conduct Apple Mail Forensics to Carve Out Evidence from Apple Mail

Apple Mail forensics is nothing but analyzing the emails from the Mac-supported email client ‘Mail’. It’s a desktop-based client where cloud-based clients such as Gmail, etc. can be configured. Investigators examine Apple Mail to extract and gather information for legal and investigation purposes. However, while doing the investigation, professionals face various challenges. Let’s first address those.
Challenges Faced During Apple Mail Forensics
Apple’s ecosystem is complex in nature. Plus, its security features act as an added shield that is difficult to penetrate. Here are some of the common challenges that forensic professionals encounter during investigation.
- Encryption and Security: For communication, Apple Mail uses end-to-end encryption. Leading to challenges in accessing the actual content of emails without encryption keys.
- Protection in File System: Mac OS is famous for its robust security features such as SIP (System Integrity Protection). It restricts access to certain system files and extracting Apple Mail data.
- Database Changes: With a software update, Apple Mail storage format and structure may change. In return, it creates difficulty in locating the exact information for the investigation.
- Change in Metadata: The frequent updates not only change the storage structure but also alter the metadata stored by Apple Mail. Making Apple Mail forensics more challenging.
- Complex Data Structure: Apple Mail stores data in complex structures such as MBOX or SQLite databases. Without having the expertise, it’s difficult to parse these structures.
- Handling Attachments: While analyzing Apple Mail, attachments play an important role. It can contain relevant information in making or breaking a case. However, encrypted or compressed attachments sometimes pose a real challenge in the investigation.
- Recovering Deleted Emails: Apple’s file management system and potential overwriting of data sectors make it difficult to recover deleted emails. In such a case, specialized tools are required.
- Change in Timestamp: Timestamp is crucial in any email forensic investigation. However, discrepancies in time zones may cause problems in getting the accurate result of the investigation.
- User Authorization: Accessing emails on Apple Mail asks for user authentication for password-protected accounts. Making it challenging to analyze the emails in terms of legal and ethical standards.
- Legal Concerns: While performing an investigation, it’s important to adhere to legal standards and guidelines. Obtaining proper authorization can be a real challenge.
General Steps of Doing Apple Mail Forensics
Any digital investigation can be successful if it is carried out by following systematic procedures. Consider the general steps while investigating Apple Mail.
- Evidence Acquisition: When examining emails from Apple Mail, it’s important to preserve the original evidence and avoid unintentional changes. Thus, create a forensic copy of the storage where Apple Mail data is stored and save it in E01 file format.
- Locate Apple Mail Data: On the Mac operating system, Apple Mail stores its data in the user’s library. The folder path goes like this:
~/Library/Mail: It’s for Email messages and Attachments
~/Library/Mail/v7/MailData: for Index and Metadata
- Apple Mail Attachments: While performing Apple Mail Forensics, don’t forget to analyze the email attachments. Because they may contain a wealth of information or can be potential sources of evidence.
- Email Metadata Information: When examining any email, email header analysis is very important since it can reveal crucial information for the investigation.
- Professional Forensics Tool: For accurate and court-friendly results, always rely on robust forensic tools. One such tool is MailXaminer. Along with Apple Mail, it can analyze other desktop-based and cloud-based email clients. (More on the tool is discussed in the next section).
- Timeline Analysis: Another important aspect that can’t be ignored during Apple Mail forensics is analyzing the timeline. It’ll help to understand the chronological order of events and reconstruct the sequence of events.
- Hash Value and Integrity Checks: Checking hash values can tell whether the integrity of the acquired data is intact or not.
- Documentation and Reporting: Document every detail of the investigation. Once the investigation of Apple Mail is done, generate a report including the findings, discovered artifacts, etc.
Now, let’s move on to discuss the perfect tool (mentioned above) steps for carrying out the investigation.
Also, Read iCloud Forensics to Acquire Data from the Cloud Storage.
Analyze Apple Mail Using the Professional Software
For doing accurate Apple Mail forensics, you need tried and tested software. Here are the software steps for your reference.
Step 1. Install the software on your device and log in using the correct credentials. By default the credentials are ‘Administrator’. (You can change it anytime)

Step 2. Create a case and click on Add new evidence.

Step 3. On the next screen, click on Apple Mail for doing Apple Mail Forensics.

Step 4. After that, apply the general settings, index settings, hash settings, and decryption settings.

Step 5. Next, the tool will show all emails including deleted ones (in red color).
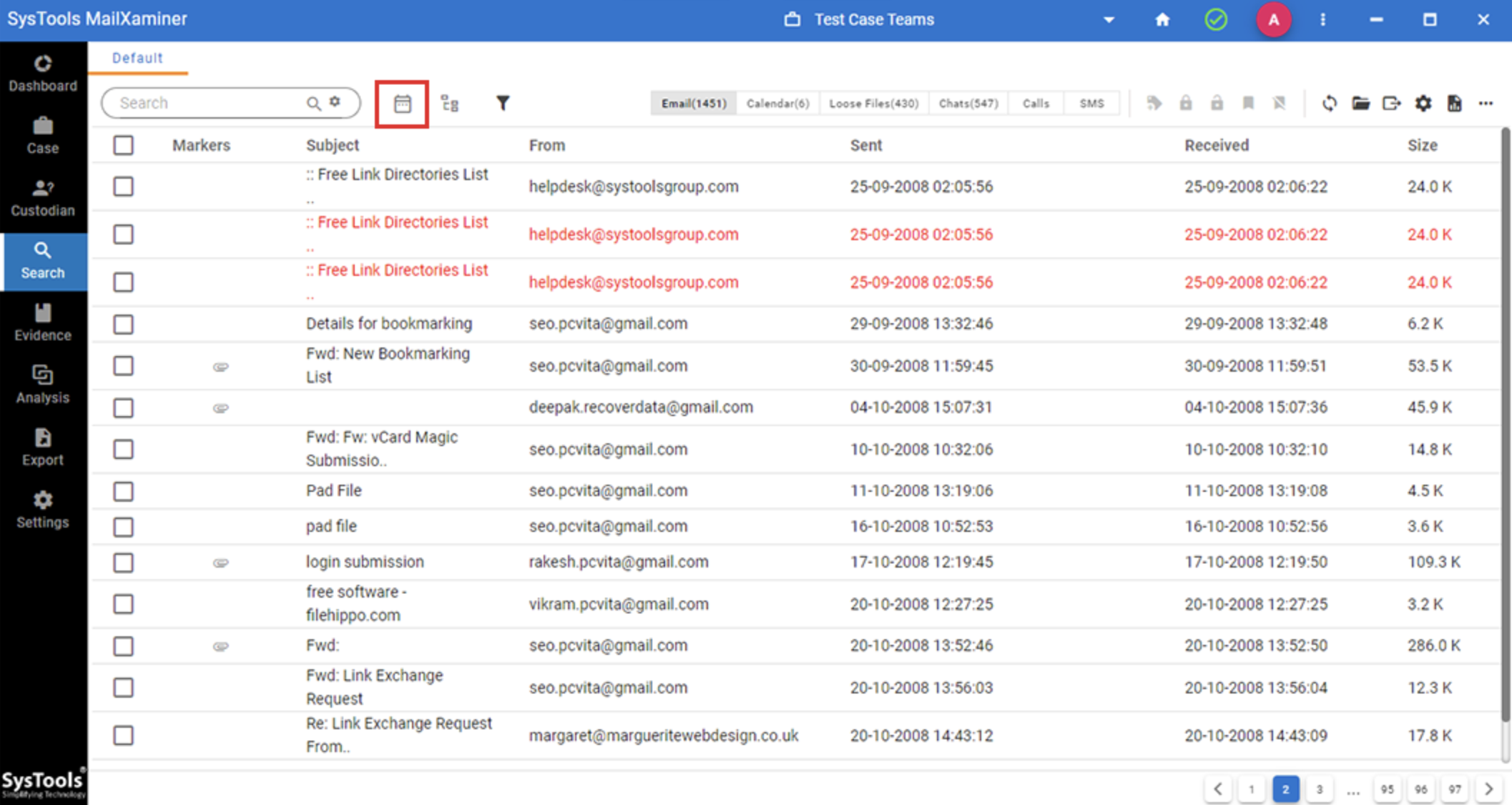
Step 6. After analyzing emails, download your findings as a report.

Conclusion
Apple Mail forensics can be a complex process if not done correctly. In this write-up, we’ve discussed what could be the challenges a forensic professional may encounter during the investigation. And, most importantly, introduced the best software and its working steps to investigate Apple Mail.


