Technology | 5 Minutes Reading
What Does the Ransomware Attack Mean?

Ransomware is a malware that seizes a user’s access to the computer. This malware circularizes like a Trojan, i.e. enters through a downloaded file or network service vulnerability. Later, a payload begins to encrypt data on hard drive & starts extorting money from the computer owner via Scareware elements.
Though most users delete chat history due to a myriad of reasons, one of the primary one’s out of which is privacy concerns. However, the culprits behind misuse of social media platforms like Facebook use deletion of chat history as their eventual escape. Nevertheless wiping off crucial messages, indecent media, etc., doesn’t always mean that you can get away with your wrongdoings. Facebook provides an unearthed tool, i.e., Archive. When the deletion of one’s Facebook messages is carried out for reasons whatsoever, it is automatically sent into the archived folder. Which means that the data is not permanently lost yet. And retrieval of those messages and media files is still possible for solving criminal cases and prevent similar crime from taking place in the future.
Ransomware and Its Functioning
Ransomware and Its Functioning It isn’t a new technique adopted by the cyber criminals to illicitly extort large sums of money from users. The first occurrence of Ransomware happened in the year 1989 as PC Cyborg Trojan. However, usage of this malware increased largely since 2005 and was delivered to the victim’s machine by the assaulters in two most common ways:
- Drive-By Transfer: This is considered as the most common ways for delivering Ransomware into a computer. You are either supposed to visit a compromised/malicious website and click on an infected link/advertisement. Or, the malware enters your computer when a malicious attachment is opened/downloaded from an email.
- Abusing Program Exposure: Similar to any malware program, Ransomware targets on attacking and exploiting the security exposures on the operating system or a program installed on it; a web browser for instance.
The Concept: Basically it is a malware which makes use of payload elements of different types to lock down a computer’s functioning. However, it is popular known as ‘Ransomware’ instead of a ‘malware’ because a sum of money (particularly enormous) is demanded back in order to regain access on the system or files on it.
What Happens: The payload generally encrypts the files present on the machine using hybrid-encryption or locks down the entire machine by making changes to the boot files. Later, a message stating that:
- Either the application that the user is trying to access has expired, a payment for which has to be made in order to access the associated files.
- Or, a fine has to be paid for visiting/making access to illegal web content (usually obscene) to suppress criminal charges from being made against the affected computer’s owner.
Variants of the Malware
There is a vast variety of Ransomware that can be classified into the following categories:
SMS Based Ransomware: This kind of Ransomware blocks a user’s access to their computer and displays a ransom message on screen accompanied by a code. The code has to be sent as an SMS to a premium rated number. Another code will be received for unlocking the machine, once the payment has been made.
File Encryptors: These Ransomwares encrypt any/all file available on the infected machine using complex encryption techniques like – hybrid-encryption. Author of the malware then demands the victim to make payment for decrypting the files. In a number of cases, the Ransomware leaves a file on the machine often known as the ransom note; offering details of how much and how to pay the ransom amount. Typically this kind of Ransomware does not lock the computer; however this isn’t a fixed condition.
MBR Ransomware: This is one more of the most popular types of Ransomware variant which surpasses all the other types in the way it locks the system. The Master Boot Record is changed in this case which interrupts a normal boot procedure of the computer. This is of the most grievous type as the victim is offered no chance to boot the system and get rid of the malware.
The Increase in Ratio
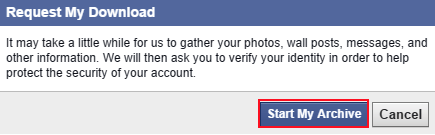
Now Request My Download dialog box will open
- Click on Start My Archive again to start the gathering process.
-
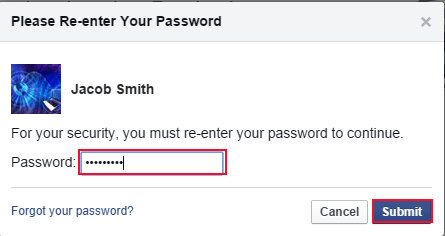
Now in next window: –
- Re-enter your password dialog box will open.
- Enter your Password.
- Click on Submit.
Avoid the Impact
The IMPACT
Payments made on the extortion basis are usually irreversible and also difficult to be traced. This is because the assaulters under normal conditions accept payment to be made only through vouchers or much worse; virtual currency which includes the currently in trend ‘Bitcoins’, Moneypak, CashU Codes, Webmoney, etc.
HOW TO AVOID IT?
- Install applications that can block out executable or compressed archive files before they can reach within your inbox or apply filter within your email.
- Update the version and patches of your antivirus program regularly and make sure a genuine and licensed copy is being used.
- Keep a regular backup of your essential files/folders on a removable media to ensure that no compromise is made.
- Make settings on the computer’s software management application to ensure that suspected programs are prevented from accessing critical directories of the system.
- Set the Group Policy Object of the computer to restrict the registry key, i.e. database consisting of settings in order to restrict malware to encrypt any data available on the machine.


