Technology | 5 Minutes Reading
Cell Phone Vulnerabilities

Smartphones’ popularity and relatively lax security have made them an attractive target for attackers. Cell phones are radio transceivers and the voice is transmitted through the air on radio waves. Smartphones and personal digital assistants (PDAs) give users mobile access to email, internet, GPS navigation, and so on. However, the security in smartphones has not kept pace with traditional computer security.
Technical security measures such as firewalls, antivirus, and encryption, are uncommon on mobile phones and vulnerabilities of these provide the entry gate for attackers. Hackers armed with inexpensive radio hardware and open source software can compromise your mobile phone, listen to your conversations, intercept your data, use your phone number to make calls that are charged to your account, and all this will happen without you being known about it. As per the info provided by some benchmarked authorities, from 2009 to 2010, the number of new vulnerabilities in mobile operating system has jumped to 50%.
As per the some popular Security Research lab, a variety of Android system vulnerabilities that threatened users in June. Hackers can take advantage of these flaws and thus the malware infections prevent users from using their phone normally and these liabilities are incredibly widespread and affecting a significant amount of Android users worldwide. Be Aware! The biggest vulnerability flaws in your Android OS are
Exposure To “Cloning” – Cyber Crooks Using Your Phone Numbers
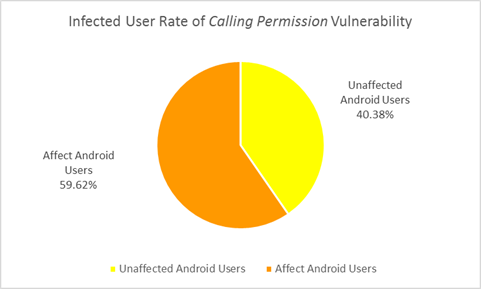
Generally, Android phones need the user’s permission before they can make the call. In July “Phone (com.android.phone)” was released and this vulnerability allows malware to initiate or end a call, or even make calls to premium rate phone numbers without first gaining the permission of the user. Hackers can easily use this bug to dial a particular number so that they can interfere with normal calls, lock the SIM Card, delete the data on your phone, and so on.
By using the cloning, hackers can intercept the electronic serial number (ESN) and mobile identification number (MIN) and program these numbers into another phone to make it identical to your phone.
Private Information May Get Leaked
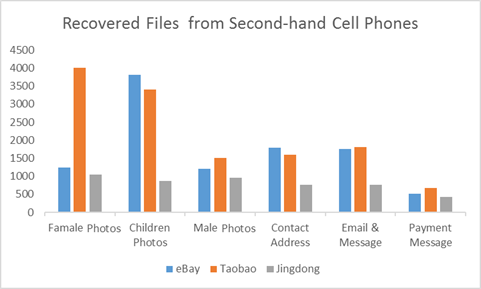
Android users should be aware of that the data available on their phones such as photos, messages, call records, history and other info can still be recovered or viewable by malicious users. If you are selling or even just throwing your old cell phone, it was observed that there are no precautions taken by the users. This weak point can affect almost all Android phones and because of that hackers can easily carve out the any personal information by using simple data recovery tools.
Usage Of “Fake IDs” – A Threat To Mobile Payment Security”
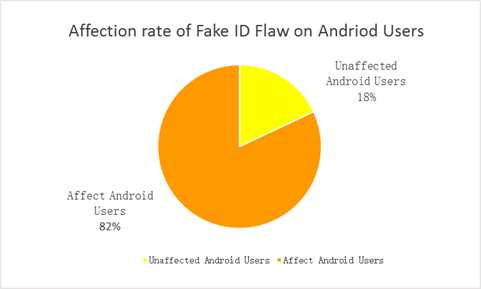
Hackers can create a malicious app that imitates trusted Android system apps such as Adobe Flash Plug-in, 3LM, and so on, and when users will use these apps, these malicious applications will then operate stealthily on user’s mobile. Using this malicious application cyber criminal can secretly steal account numbers, passwords and other private information.
Android System’s Weakness To Being Used As A Microphone
Android phones can be turned into a microphone and transmitter for listening to the conversations in the vicinity of the phone. This can happen by transmitting a maintenance command on the control channel to the cell phone. This command places the cell phone in the “diagnostic mode” and after that conversations in the immediate area of the telephone can be monitored over the voice channel. The user does not know that the telephone is in diagnostic mode and their conversation is being recorded by hackers.
Steps To Protect Your Android Mobile Phone
- During choosing a mobile phone first, check its security features: – Before selecting the Android phone, check the offers provided by device such as; file encryption, the ability for the provider to find and wipe the device and many more. Also check the authentication features such as passwords to access device.
- Organize the device to be more secure: – Most of the smartphones provide the feature of locking. Users should enable this feature to protect their device. Enable encryption and antivirus software if existing.
- Configure web accounts: – Many popular and social networking sites provide the option to use encrypted connections such as HTTPS (Hyper Text Transfer Protocol Secure) or SSL (Secure Socket Layer) in account options pages. User can use this feature to protect their phones from hackers.
- Do not click on the links sent in dubious emails or text messages: – Click on such links may lead to spiteful activities.
- Revelation of mobile phone number: – User should think carefully before displaying a mobile number on social networking websites. Attackers can easily collect the information like phone number, email address, etc., from those websites to commit crimes.
- Think before store your personal information on the device: – When user store personal information on smart phone; then think carefully, an attacker could obtain such stored information.
- Choose correct apps: – Before selecting and installing any apps do a little research on them. Do not install the apps directly that provide attractive packages; it may contain a Trojan horse.
- Disable interfaces when not in use: – Interfaces such as Bluetooth,infrared and Wi-Fi should be deactivated in public places. Criminals can easily deed vulnerabilities in software that use these interfaces.
- Do not “root” or “jailbreak” the device: – Now, smartphones are available with inbuilt antivirus features. But sometimes a user changes the default setting of firmware that alter the malicious code or unintentional security vulnerabilities.
Mobile data vulnerability occurs for a number of reasons, including poor security practices and procedures, inadequate training for individuals responsible for network security, or software products of poor quality provide the entry gate for attackers. One of the research shows the statistical data of an alarming increase in susceptibility mobile data. Using the serious code security audits and exploit mitigations by the major baseband chip, vendors can go a long way toward reducing this type of security problems.


