Technology | 6 Minutes Reading
About Data Sanitization , Redaction & Cleansing Methods

As technology advances day by day, data security becomes one of the biggest concerns of cyber authorities. In order to secure data, we need to either protect it or mask it from getting misused. To secure the data, we need to understand the audience first as bigger the audience grows the higher the security shields should be deployed.
Data Sanitization defined as the process of editing high priority database or documents where crucial data stored needs to be securely concealed. Critically acclaimed as an anti – forensic method, the process can be either erasing the information off the records completely or display the information masked from the unauthorized users. The process can be traced back to the time when we didn’t have computers. People used to hide information by masking them efficiently such as in case of maps information used to be hidden to protect treasures from getting revealed. Following could be achieved with data sanitization :
Redacting Valuable Information
- Sanitization techniques are mostly used by Government bodies where there is a need to maintain secrecy amongst the legal documents. Typically they use an entrusted process which deals with editing contents or camouflaging the sensitive information in the original document instead, known as Data Redaction. This method makes use of smart and intelligent techniques which makes the general audience unaware of the information but on careful examination the secret piece could be unearthed.
- Earlier techniques were not that successful as some information got visible due to inefficient placement such as in word documents, changing color of the secret information thus matching it with the background color to make it invisible to the readers soon got flop as users sooner came to know how to find the text hidden using search selection methods. However a solution that was: preserving the documents in PDF format was used as an alternative where secured features could be deployed easily.
Data Redaction technique is however done under supervision and constructed under the guidelines of governing body. Important factors such as pointing out the text or data redacted should be well mentioned and verified according to the norms. Maintaining a local record of the original document getting redacted is a mandatory act under this process as law requires both the documents to be present while presenting a case. Data Protection/Data Cleansing Act here serves as the guardian of data to be sanitized and has several acts mentioned so that the sanitized data doesn’t remain invisible to the law but gets redacted efficiently for the target audience.
Data Protection
The digital media spread offline and online is quite cumbersome to sanitize as machines oppose the need of data sanitization / data erasure. Machines built to store and create data follow a simple norm that is to retain the data no matter what the condition is; this makes the cyber world a harsh reign to conquer. While modifying or erasing digital information, some or almost every bit of the previous data kept accessible in the storage. Storage mechanism as RAM keeps a local cache of the data in order to maintain easy access & high speedy performance of the machine. This allows users to retrieve redacted data access easily despite normal erasure.
Machines are backed up by large number of data retention techniques researched & adapted over time. Preserving a data cache, hard backups, cloud backups, undo buffer, trash can & maintaining a revision history are amongst the few techniques data backed by. When we delete or modify the data it is only erased from the Index, the actual data still resides in the physical disk and takes a large amount of time to wear off permanently. These orphan data can be easily traced and restored back.

Even when we are interchanging information in any form that might be offline or online leaves multiple traces which makes the sanitization a tough job to excel. Techniques such as removal of Meta data, shredding or wiping clean the revision history serves as a solution to some extent. However remnant Data is a hurdle which only data sanitization can conquer.
The process often tried to establish using the operating system residing on the target storage media, it is nearly impossible to do that securely. The media should be detached and sanitized on a separate operating system consisting of administrative rights to access the possible memory locations on that disk.
Effective Sanitization Methods
Whenever we try to approach sanitizing data the first step that comes logically is to either add an extra layer on top of the information or cloaking the data to make it invisible. Both the techniques fail as the data is still present in the storage media/document. The feasible technique data is to either modify the Meta data or redact & create a fresh copy of the data. But we need to achieve elimination of remnant data, to do that we need to follow proper authorized techniques such as:
- Purging – Hard deletion(data cleansing) of data in such as way that it is beyond recovery and leaves no traces, it ensures that no remnant data is left.
- Degaussing – It is the method of purging or sanitizing the data by reducing the magnetic field of the storage device with the help of a device known as degausser. Government bodies use this method to remove complete traces after redacting data from original source to a secure location.
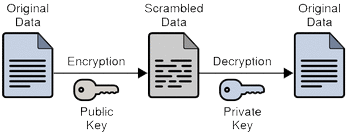
- Encryption –It is considered one of the safest methods to sanitize a data as using specific keys to lock certain portion of the redacted data would be invisible but on provision of proper key, the data is visible to the authorized body.
- Overwriting – It considered as the fastest and cheapest sanitization method. But, the security of the remnant data is very low as it is quite easy to make out what changes were made.
- Destruction – Physically shredding/destructing the storage data ensures that there would be no possible way that the data could be retrieved further.
Government bodies posed proper penalties on improper sanitization techniques as classified information possess a risk of leakage causing multiple issues to harm them respectively. Some nations declared legal penalization up to imprisonment, if either the data is not sanitized as per the guidelines or gets leaked somehow.


