Uncategorized | 3 Minutes Reading
What Denial of Service (DoS) Attacks Symbolize!
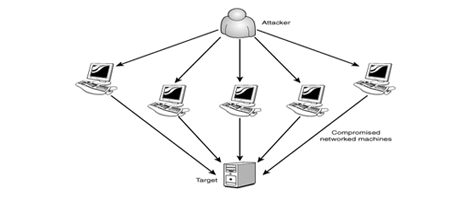
DoS is an acronym for “Denial-of-Service Attacks”. It is also known as DDos i.e. Distribute Denial-of-Service Attack. DoS is an action of making a machine or a network resource engaged and unavailable for its anticipated users. This network attack temporarily interrupts the intended users from gaining access to the targeted network resources.
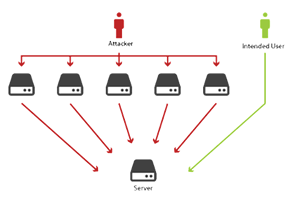
The assailants performing the DoS attacks, generally target sites or services hosted on crucial web -servers such as; banks, payment gateways, security intelligence, etc. An explicit attempt by the attackers that may prevent the legitimate users from accessing the resources may include: Flooding a Network with multiple requests. Thus, preventing the legitimate traffic. Disrupting the Secure Connection between the source and target machines. Prohibiting a Particular Individual from gaining access to a service. Disrupting the Functionality of the complete system.
Denial of Service Attacks
As per the Internet Architecture Board’s Internet user policy, the Denial-of-Service attacks are illegal and tend to violate the guidelines of the benchmarked policies laid down by the Internet Service Providers. The above mentioned examples show that DoS attacks can be executed in various manners. Three basic modes using which attackers perform Denail-of-Service attacks are listed below: –
- Consumption of scarce, limited, or non-renewable network resources.
- Complete destruction of the original configuration of the network.
- Physical devastation of the network components.
Illegal Consumption of the Network Resources
The lifeline of the network resources includes network bandwidth, memory and disk space, CPU time, etc. The DoS attackers or network attacks, target these resources and prevent the intended users from accessing them. For example, in “SYN flood” network attack, the intruder tries to create a connection with the victim’s machine and over consumes the kernel data structures which are a crucial resource for establishing network connections. The intruders may also consume the bandwidth of your network. This is generally done by generating a large number of data packets transferred towards your network.
In addition to network bandwidth, the DoS attackers may also consume many other crucial resources. Some of the systems have a very limited number of data structures available that are meant for holding information. The attackers may generate a certain type of script of code that has the caliber of creating duplicate copies of all the data stored in a data structure. Thus, destroying the available space.
Network Attacks
The place that the intruders love to target is the user’s machine. Any sort of alteration in the machine’s configuration may disturb the whole functionality. The most common job that the attackers perform in this type of case is, altering the routing information of the routers. The attackers may also target the registry of the Windows NT machine.
Physical Impact
One of the most basic issues that needs to be focused and properly cared about is, the physical security of the devices. Proper measures and all the possible precautions must be taken to ensure the safety of computers or devices. These physical artifacts include computers, routers, network wiring chords, etc. The local or international law enforcement agencies prove to be very helpful in this scenario. This type of Denial of Service attack or network attack often leads to heavy loss of capital and other resources.